I had an amazing opportunity to be invited as a guest “Expert” with B2B Tech Influencer, Evan Kirstel, and Hardik Jain, CTO and Co-Founder of GXC to discuss how 5G is making trusted wireless connectivity simple.

GXC is a lesser known vendor in the Private Cellular industry, but they are building some cool stuff. They are mainly a 5G Core vendor with some cool things on the RAN side. Their core is called the GXC Onyx Core and operates like most 5G cores.
There is a good overview between GXC’s Private Cellular Network and Wifi over on LinkedIn. “As technology continues to advance, private cellular networks enable innovation, not to compete, but rather to complement Wi-Fi, addressing the specific requirements of applications and services beyond the traditional network capabilities.”
I have a close friend that works at GXC. So, I have been following their progress quietly in the background for a few years now. They have carved out a little niche that has some use cases that many in the industry aren’t aware exist. I’ll explain that niche more in depth in a future blog post. I’m awaiting their radios to test out before I want to talk in depth about that niche.
You can catch the Livestream here:
GXC is best known for their Private Cellular Mesh Technology. They have built their radios to function as a Mesh node if the use case calls for it. The radio can connect to another basestation radio for the uplink, then it can rebroadcast to additional clients that are further away from the main basestation.
We do this a lot in our homes with Wifi because we have a limited number of clients vying for airtime on the Wifi network, although throughput is cut exponentially with each node added. If you bring Wifi Mesh into an Enterprise environment, you may suddenly find your Wifi network is almost useless because of so many clients fighting for airtime.
Cellular, because of the ability to schedule who is talking, is much more efficient. This allows the usage of Mesh to be more efficient as well. I’ll talk more in depth about this when I get some of their gear to play with and can do some hands on testing.
During the Livestream, we discussed many aspects of Private 5G/LTE Networks that are being built today, and what’s on the horizon as Private 5G continues to be used by more organizations. Our main discussion was about how Private Cellular can be more secure than most Wifi networks.
Security and Private Cellular
We talked specifically about the security of Private Cellular vs Wifi. Ultimately, Private Cellular is more secure in certain ways.. BUT saying that Wifi is less secure isn’t necessarily true. Just by building a Private Cellular network doesn’t make your network more secure by itself.

IMSI Protection
When it comes to Cellular Technologies, 5G is more secure than LTE, which is more secure than 3G, which is more secure than 2G.

The usage of the IMSI in LTE can be captured with a Simple IMSI Catcher. When an attacker has the IMSI, it reduces the privacy of your Private LTE Network. Anyone can build an IMSI Catcher with a cheap SDR and a Raspberry Pi or a Laptop. Once an attacker has your IMSI, they can track your client reducing privacy. The IMSI doesn’t provide access to the user encrypted traffic but it does reduce privacy. With Private Cellular, an attacker could use an IMSI Catcher to find when a user is onsite or not.
At DEFCON 31, I was specifically interested in this presentation during Day 0. Tracy Mosley went through the history of the Core Networks and some of the vulnerabilities of all the Cellular Generations. At DEFCON 31, they also had their first Telcom Village, where some of the attacks against 2G, 3G, LTE, and 5G were discussed and demonstrated.
5G prevents some of these issues if you prevent your devices from downgrading to a lower Cellular Technologies like 2G or 3G. In the CBRS world, most installations are going to be LTE or 5G, so anyone installing Private Cellular should be disabling clients from downgrading to 2G or 3G that aren’t roaming on the carrier networks or internationally. Most 2G and 3G networks have been sunset within the United States, although they are still in use internationally.
5G introduced the SUPI, Subscription Permanent Identifier, which is the 5G replacements for the IMSI ,and the process to conceal the SUPI, called the SUCI, Subscription Concealed Identifier. These two together are built to prevent IMSI Catchers attacks. BUT 5G has some new vulnerabilities that are discussed in the video above from DEFCON 31. 5G as a technology is much more secure, but it isn’t without its flaws.
SIM Cards and Encryption Keys vs. Wifi
The Encryption, because of the use of SIM cards that handle the distribution of the Encryption Keys to devices, is extremely challenging to decrypt. Almost all modern attacks against Cellular are targeted at the Client or the RAN/Core Network. The same goes for a properly configured WPA3-Enterprise Wifi network.
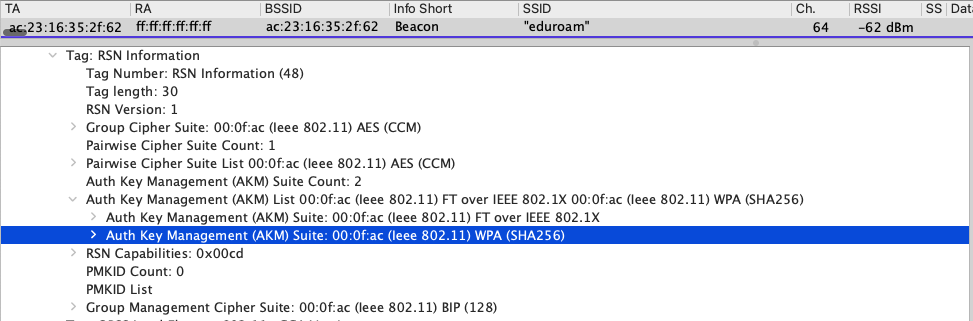
If you have a good WPA3-Enterprise Wifi network using device or user based Certificates in a Zero Trust model, you are achieving many of the benefits of Private Cellular. The challenge comes down to how you are distributing your keys and ensuring those certificates are not being stolen and used by someone else. It is also important to have a Zero Trust model for access to all resources in case someone gets access to an active SIM.
Working with schools, we are fighting this battle regularly on our Wifi networks. A teacher, who is also a parent, put their work credentials on their child’s device and suddenly the child is connected to the teacher network. All “protections” of that child are suddenly reduced to the level of the staff.
Cellular is absolutely more secure in a technical comparison against Wifi that uses WEP (long broken.. STOP USING IT!!), WPA-PSK or WPA-Enterprise (Don’t use either), Open System, WPA2-PSK, OWE, and WPA3-SAE. WPA2-Enterprise, using certificates with proper key distribution and ensuring that Protected Management Frames is required, brings you closer to the level of protection of WPA3-Enterprise, since they are very similar. The issues with WPA2-PSK and WPA3-SAE, are that there is a shared passphrase that anyone can get through various means and suddenly they have access to the Wifi network. Cellular prevents that because of the SIM to a certain level…
Cellular provides mitigations for all these issues.. BUT there are equivalent issues that many are not considering when building a Private Cellular Network.

When it comes to security and Private Cellular, SIM management is critical. In the Cellular world, there are protections built in to the core and SIM to prevent SIM spoofing. So, cloning a SIM can be mitigated fairly easily today. It is currently impossible to get the Ki Key off of a modern SIM as explained in this video. Many Cores are also built to not allow the same credentials to be used by two SIM cards at the same time. We found that out during some testing at a security conference that I’ll talk about a little later.
The issue that comes up with SIM Management is that with many Private Cellular deployments, SIMs are NOT being locked to only work in a client device, through SIM Locking.
What is stopping an attacker that has physical access to a client from removing the Physical SIM and putting it in their own device? This is even more important when it comes to Private Networks because we are using SIMs as authentication to network resources. Carriers mainly provided access to the Internet and voice calling; so, they don’t always enable SIM Locking because of the burden it puts on the general public. Most of the time, you are able to remove a SIM and put it in another device with little issues. Private Cellular networks are providing access to internal company resources, which opens a whole new floodgate of access restrictions.
In initially building our Private Cellular network for schools, we had this come up. We send a device home with a student so they can do their homework. Some parents, knowing that a SIM gives them connection to a cellular network, would remove the SIM from the device provided and put it in their personal cell phone to get free data. That parent with their personal device is then inside our firewall with the ability to access the resources we thought were being protected.
What is preventing a staff from using your cellular network for their personal data plan? What is preventing someone that is frustrated with your company from removing the SIM card and placing it in their personal laptop and exfiltrating company data or installing applications on your internal equipment?
Unless you have SIM Locking or are using an eSIM, there is nothing other than Zero Trust or firewalls from preventing that attacker from gaining access through physically removing the SIM. Lock your SIMs to clients! In my conversations with GXC since the Livestream, they now have that functionality built into their system.
RAN/Core Security
RAN and Core Security are critical pieces that must be considered during the design, planning, and implementation phases. The radios being released today were designed to be used by a large carrier. Some of the firmware doesn’t have protections that many enterprises require of their hardware, such as removal of default passwords or other issues.
Code Issues
If someone gains physical access to a radio site, they often are inside your firewalls. Just like we need to protect Wifi APs from physical tampering, ensure protections for your cellular radios.
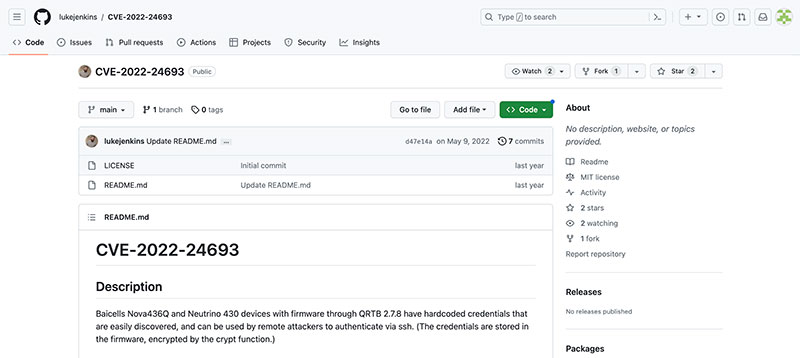
During our build out of our private LTE network, we found many issues with physical security. One example that is now fixed in updated codebases, is the inclusion of hardcoded credentials in firmware. My good friend and colleague, Luke Jenkins, found and got a CVE for specific Baicells code, CVE-2022-24693. We worked with Baicell and they ended up fixing this issue and others that we reported. They are now doing a better job at secure coding their firmware.
Be aware, this isn’t happening across the industry yet because those installing the equipment are not demanding it. This is improving but not solved! Many vendors will whitebox and resell Baicell radios. They may or may not write their own code or at least reuse some of the original code for those radios. These issues may be introduced into additional firmware.
Physical RAN Security
The other issue comes down to physically security of your RAN network. Every year, I attend my favorite local conference some of my colleagues put on, called SaintCon. It is a local security conference made up of many of the local Goons from DEFCON. At SaintCon, I’ve presented many times about various things related to education security.
In 2021, we had a contest at SaintCon, were we let attendees hack our Private Cellular network. We had various CTF challenges to see if people could access different parts of the network and gather certain pieces of information. We weren’t using our production network, obviously, but we had a full Core Network and RAN available for hackers to play with.
During the conference, we helped attendees program their own SIM card. Obviously, since it wasn’t our main network, we used junk data for the keys, such as 00112233445566778899 for the Ki, as you can see below.
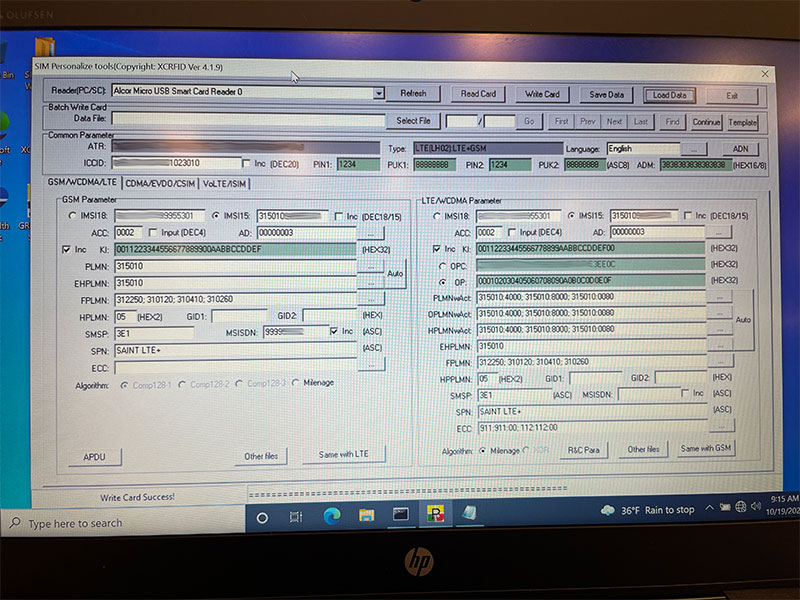
We let attendees select a number within a certain range for the last few digits of the IMSI.. As it happened, several attendees selected the same number in that range. The second person to use a number was unable to connect to the network. As I mentioned about SIMs before, many Cores won’t allow multiple SIMs, with the same information, to connect at the same time.
While programming SIM cards was the most attended part of the challenges, we gathered some interesting data from the event. For attendees, most of the successful data was gathered through social engineering those of us running the event. There were only a couple teams that got other parts of the challenge through actually attacking our network.

One team got onto our core network through putting a physical network Tap between one of our Radios and the backbone to the Core. LTE and 5G use encryption between the Radios and the Core for most traffic so most of the information was protected. BUT they got certain internal information such as data about how the network was designed and other issues. Had they had more time and more knowledge about core networks they probably could have gathered more information and gained access to more resources INSIDE our firewall.
As you build your private networks, ensure protection including segmentation for these physical RAN locations and coding issues.
Private Cellular Security Landscape
Talking with Hardik and Evan was an excellent experience. As was mentioned during the Livestream, we need to educate the network engineers installing these technologies. They are being told that it is more secure without realize the potential issues.
The industry is finally starting to catch up. Vendors are starting to listen and creating secure firmware. SIM Locking and the rollout of eSIMs are reducing the impact. Then new technologies like 5G are bringing new protections but are opening additional issues. The promise of more secure wireless technologies are here. Private 5G and WPA3-Enterprise Wifi are providing pretty good security if properly installed.
I hope to hear more from GXC next week during Mobile World Congress 2023 in Las Vegas.


