It’s been just under a year since I started my series on eduroam and WPA3-Enterprise requirements in 6GHz. There has been a ton of people that are rolling out 6GHz eduroam and have data to compare against my initial testing. As time rolls on, clients that do not support WPA3-Enterprise continue to be phased out. At WLPC Prague back in October, I gave a TenTalk where I briefly discussed some of those findings. These finds can also be applied to Wifi 7 as these requirements have not changed from Wifi 6e.
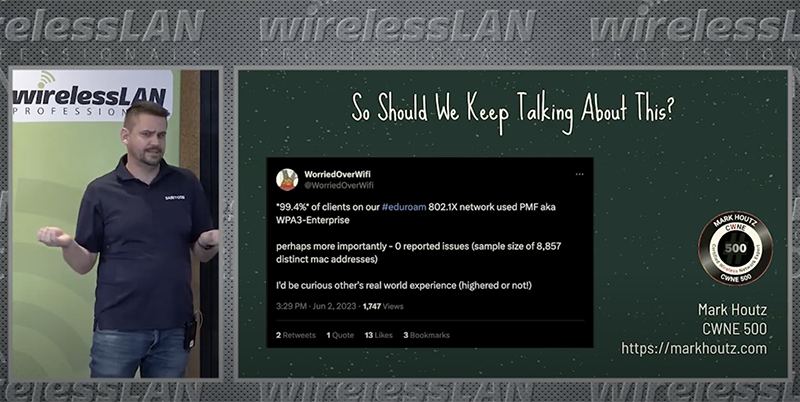
To follow up my series and give an update, I wanted to write a quick post discussing what the community and I’m are seeing. I also want to dig into some things that the industry needs to implement to better secure these eduroam networks.
Recap
In my series, I discuss several issues and tests that I conducted with eduroam and WPA3-Enterprise. When you enable 6GHz on an eduroam SSID, depending on the vendor, you are required to use WPA3-Enterprise on 2.4 and 5GHz without Transition Modes. Before enabling 6GHz, there is a Transition Mode available that goes away when you enable 6GHz.
The reason for my testing was there was a fear of rolling out eduroam on 6GHz because it requires you to set WPA3-Enterprise on the 6GHz band which also brought the requirement to the 2.4 and 5GHz bands. Official recommendations from eduroam called for the use of Transition Modes.
There was only one vendor doing transition modes when I started my testing, Juniper Mist. Other vendors have followed Juniper Mist that now allow a WPA3-Enterprise Transition Mode on some versions of their products.
You can read up on my previous testing and posts here:
eduroam + 6Ghz + WPA3-Enterprise (Part 2)
eduroam + 6GHz + Vendors (Part 3)
eduroam + WPA3-Enterprise + Clients (Part 4)
Executive Summary: WPA3-SAE and WPA3-Enterprise Client Support
WPA3-Enterprise vs WPA2-Enterprise
The big difference between WPA3-Enterprise and WPA2-Enterprise is two things as I talked about in those articles. Protected Management Frames (PMF) are required and there is a new Security AKM. Transition Mode (only on the 2.4/5GHz side when used with 6GHz SSIDs) introduces some possible issues on really old devices. I tested some devices that do not understand the new AKM and decide to just fail.
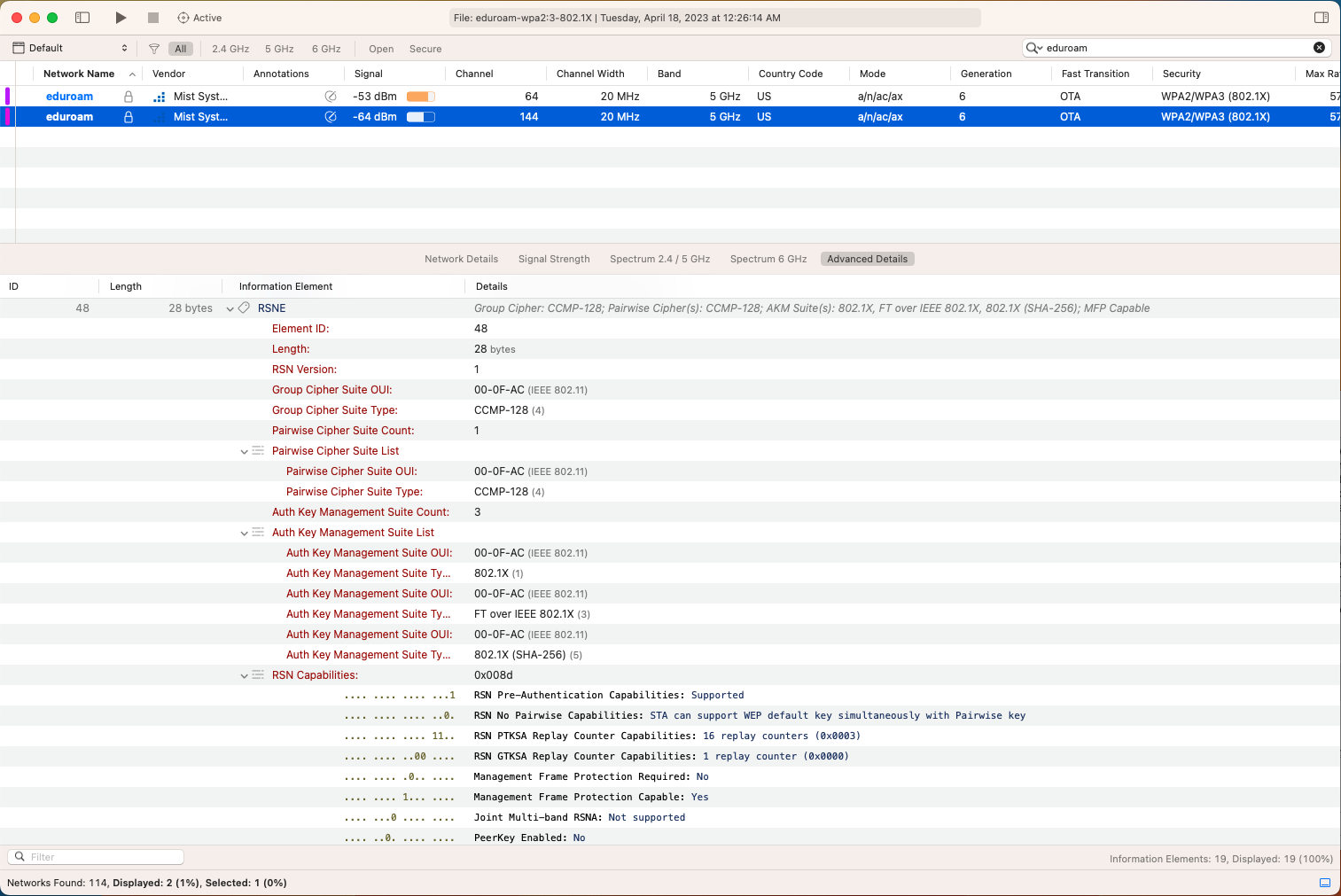
After a year of testing, as I mentioned in my presentation in Prague and as was mentioned by Wes Purvis and others, WPA3-Enterprise is very safe to implement, especially if you implement the Transition Mode if you have concerns about really old devices.
The security benefits are critical, so implement WPA3-Enterprise until you can’t; then implement WPA3-Enterprise Transition Mode until you can’t.
Criticisms of my Previous Blog Posts
I just want to quickly address some criticism and clarify a few things from a specific person I won’t name regarding my previous posts, Heavy Wireless episode with Keith Parsons, and my TenTalk at WLPC Prague. Anytime, I post about this topic, I get criticism from this person that this is a non issue. Lee Badman had a recent article about another topic calling out some issues with said person. I typically don’t like to feed the trolls, but figure he will probably continue to make these comments without actually reading this far, so I want to address it.
One of the criticism is that we shouldn’t be implementing Transition Modes because WPA3-Enterprise has such wide support that this is a non issue. (The official title of my Prague TenTalk was “eduroam, Can We Stop Talking About it Yet?“.. this is my last slide.. I want this to be a non issue; so, we can stop talking about it.)
For those of us in the trenches actually installing these eduroam networks, there has been a real fear, and at the time few had publicly tested these things out prior to my testing. Vendors may have conducted extensive testing internally, but only Wes Purvis from Juniper Mist was talking about them publicly before I did my testing.
I can’t remember who said this, I think it was Jim Palmer in a private conversation before WLPC Phoenix, but whoever said it explained it perfectly. Covid and the product shortages hurt Wifi 6e because these kind of things are usually fleshed out in the early days by the community and vendors. Covid stretched that timeline out to where the vendors were unable to get that feedback to potential issues as few could get their hands on gear for these types of testing.
Said critic is largely correct in his assessment, but he didn’t publish any articles or blog posts showing real world testing to ease the concerns in the community. Trolls will troll.
Ultimately, many of these concerns in the community came because there are issues with migrating to WPA3-SAE or the Transition Modes. In our community we often don’t spell out WPA3-SAE or WPA3-Enterprise and just lump them both under the single name WPA3. So there was a lot of confusion that eduroam was plagued by issues with WPA3-SAE which it doesn’t use. During my Podcast with Keith Parsons on the Heavy Wireless Podcast, even our discussion started with a brief question from Keith about this issue with reference to WPA3-SAE not WPA3-Enterprise. I purposely always spelled out WPA3-Enterprise in my previous discussions to help mitigate this communication issue.
Finally, said critic often bases his criticism on the fact testing is often done on really old Gen 1 Microsoft Surfaces. I’m not the only person who has used this device to show the issue. Personally, I only used it in my testing because it is a known device to have these issues, that can’t receive updates. The problem with this fallacy that I was attempting to show is that there may be devices out there we don’t know about. He is correct in that these are very few and far between and updates can fix a lot of them, if clients still can get updates.
These device may exist in the real world on education campuses implementing eduroam. I have organizations I work with that have old devices that fall in this unsupported but still used category that fail with WPA3-Enterprise. They still exist but are hopefully being phased out sooner than later. Phasing them out isn’t as easy as a vendor like this critic would hope though.
Lastly, I didn’t conduct my testing to find which devices supported it or not. I instead approached it differently because of my very limited budget. (I haven’t made any money off this blog ever, and all testing is out of my own pocket other than getting gear for my lab at conferences or vendors sending me gear for testing.) My goal was to discover how Operating Systems (MacOS, Windows, Android, iOS, etc.) would handle the issues if they didn’t support the technology. I focused less on specific client hardware, but I took a more general look at the underlying operating systems that are the real issue.
Vendor Support
As I mentioned before, Vendor Support for a WPA3-Enterprise Transition Mode has grown. Since I wrote those articles, Cisco added the option to DNA Center but not to Meraki. I talk briefly about that and show off some screenshots from testing it in my WLPC Prague TenTalk presentation video above.
Currently, Juniper Mist, Aruba, and Cisco support Transition Mode. If you have a concern about this issue, you can now use Transition Mode and you should have pretty good support. Other vendors, like Extreme have not implemented a Transition Mode, although Mr. Multipath, David Coleman, talks about this issue all the time. It’s getting to the point where there are limited cases where Transition Mode is needed.
The security benefits are critical, so implement WPA3-Enterprise until you can’t; then implement WPA3-Enterprise Transition Mode until you can’t.
Real World Testing
Rowell Dionicio, from the Clear to Send podcast, implemented eduroam on 6GHz. He started with Transition Mode but found that all of his organization’s devices were joining with WPA3-Enterprise. He felt comfortable, as he has discussed on Youtube and on the podcast, that they implemented the full WPA3-Enterprise minus Transition Mode without an issue.
That is just one organization’s experience. I’ve heard similar testing from other organizations.
Luke Jenkins and I helped bring eduroam to WLPC Phoenix on WiFi 6e. It was the only attendee facing SSID on 6GHz. It worked like a charm without issues. Luke at WLPC Phoenix talked about the setup, results, and some additional things I mentioned in that WLPC Prague presentation video. Luke’s presentation is here:
I currently have WPA3-Enterprise Transition Mode on eduroam running across the K12 schools that I support and don’t have any issues that I have discovered. Almost all devices are actually joining with WPA3-Enterprise.
Transition Mode Draw Back
There is one draw back with Transition Mode that I am discovering. There are clients that are joining eduroam with WPA3-Enterprise Transition Mode enabled that have one issue. These clients connect with WPA2-Enterprise although they are newer clients that should connect with WPA3-Enterprise. The clients see both AKMs and still choose WPA2-Enterprise. This is the issue with the Transition Modes. I’ve only seen a single case.
Transition Mode does limit the security of the network as is expected. Historically for eduroam, the focus is less on security (more on that in a minute) and more on wide support connecting students. If a client connects to WPA2-Enterprise, we just don’t have PMF being required. PMF can be used by a client on WPA2-Enterprise which makes the security almost the same, if a client choses to connect with WPA2-Enterprise when a Transition Mode is used. This is pretty rare but can happen.
The security benefits are critical, so implement WPA3-Enterprise until you can’t; then implement WPA3-Enterprise Transition Mode until you can’t.
With eduroam, there are some things regarding security that need to be considered more importantly than WPA2-Enterprise vs WPA3-Enterprise.
EAP Security Keys with eduroam
These networks are build by engineers and IT departments with varying experience with 802.1X. For many, this could be their first experience with building a 802.1X network. Unless you implemented RADIUS for dial-up networks or have implemented a wired 802.1X network or have other Wifi networks using RADIUS, many engineers just don’t have the experience of building an 802.1X network. Make sure your implementation is using a modern EAP type, EAP-PEAP, EAP-TTLS, EAP-TLS, or EAP-AKA. Other version are known to be insecure and are be avoided.
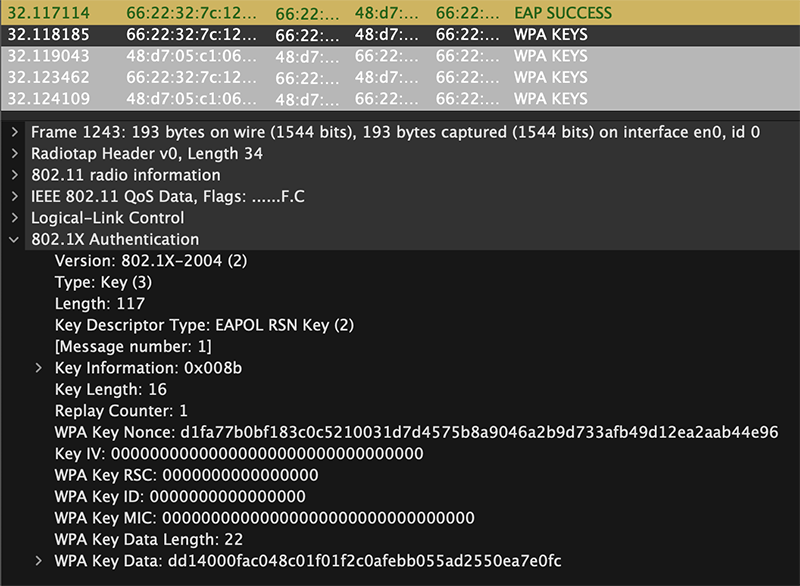
We are using 802.1X; so, the Security Keys are derived more securely than WPA2-PSK. The Keys are derived the same for both WPA3-Enterprise and WPA2-Enterprise. It depends on the EAP type used, not the version of WPA-Enterprise. Using a modern EAP type, such as EAP-TLS, the security keys between WPA2-Enterprise and WPA3-Enterprise should be secure. Those keys should be protected from attack over the air.
The security issue with WPA2-Enterprise comes from Protected Management Frames (PMF) not being required. When PMF is not required and used by a client, an attacker can use Deauthication frames to attack a client to get it to join another network. Once a client joins the attacker’s network, the attacker can hit a client with other directed attacks.
Implementing RADSEC
Most organizations implementing eduroam are still using regular RADIUS instead of RADSEC. RADIUS is an unsecure protocol that was created in 1991 and shouldn’t cross other untrusted networks like the Internet. RADSEC on the other hand creates a TLS Tunnel for passing all credentials security across any network like the Internet. RADIUS traffic can be sniffed in the middle on say the internet, RADSEC cannot.
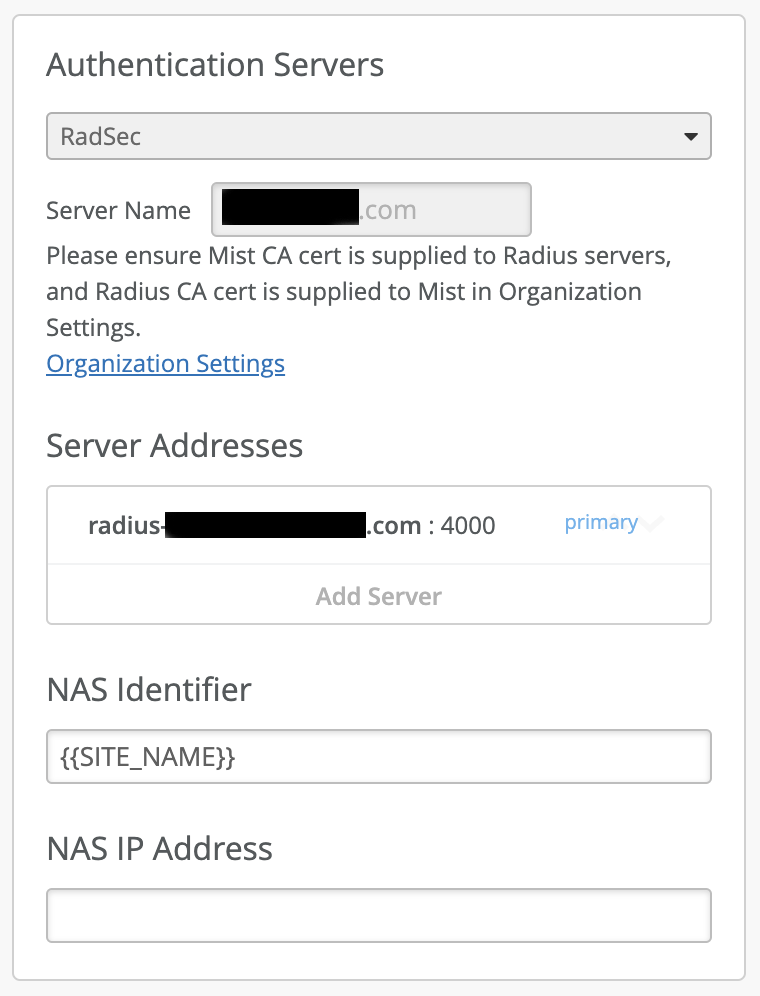
The national eduroam brokers have to support RADSEC is the one major drawback currently preventing the rollout of RADSEC to eduroam. Internet2, here in the United States, doesn’t support RADSEC yet. (I heard a rumor that RADSEC support got back burnered by Internet2 because of K12 schools like me implementing eduroam.. if that is the case, I’m sorry!) I’ve heard the European organizations do have support for RADSEC. Using RADSEC requires the use of certificates to authenticate AP/Controller and RADIUS servers to setup the TLS tunnel, just like any webserver to client that uses TLS on the internet.
We need to start pushing the eduroam brokers and Wifi vendors to rollout RADSEC support. Many of the Wifi vendors already have RADSEC support.
Microsoft and EAP-PEAP MSCHAPv2
Also, there are a lot of organizations still using EAP-PEAP MSCHAPv2. Microsoft has decided to mark EAP-PEAP as unsecure and is blocking support by default through Windows Updates in Windows 10 and 11. Many organizations are having to make a registry change to continue to use EAP-PEAP with Windows and eduroam. The insecurity of EAP-PEAP is still debatable if using proper passwords. There very much still is, as is expected, a risk if using weak passwords.
User Privacy Protection
Lastly, there also should be an external identity or anonymous identity in additional to the internal identity for providing privacy protection to our users. When someone comes on my eduroam network, my APs record the user’s username such as [email protected]. I know specifically who joined my network and where they received their credentials. This is a privacy issue that has been solved by eduroam.
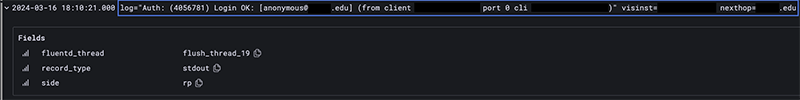
Organizations can implement an Anonymous external identify such as [email protected]. Organizations who have this setup prevent me from knowing specifically who authenticated to my network.. BUT there is still a way to identify users. The inner identity still identifies the user to their home RADIUS server.
If there is abuse on my network, I can reach out to the home organization as I still know the user came from @university.edu. The RADIUS server at the home organization should be logging that authentication to another RADIUS server that can track the user if needed. It’s not true protection for user privacy but helps. The extra steps will deter most from the extra effort.
To properly build a secure eduroam network, we need to be using RADSEC with EAP-TLS. This isn’t an easy lift and has been why many haven’t shifted yet. Implementing Certificates is more complex to rollout and scares a lot of tech departments away.
Conclusion
Ultimately, as I discussed in my presentation at WLPC Prague, moving to full WPA3-Enterprise is fairly safe with eduroam. Roll out WPA3-Enterprise Transition Mode if you are worried about eduroam and clients supporting WPA3-Enterprise.
The more important issue, is to look at the additional security things needed for eduroam. We need to start pushing the eduroam brokers to support RADSEC. Our users deserve privacy functions to be built out. We also need to begin looking to move on from EAP-PEAP to EAP-TLS.
As I’ve said several times..
The security benefits are critical, so implement WPA3-Enterprise until you can’t; then implement WPA3-Enterprise Transition Mode until you can’t.


