DEFCON 31
I had the privilege to attend DEFCON 31 in Las Vegas last week. DEFCON is one of the wildest and irrelevant conferences full of hackers where almost anything goes. Researchers and Hackers get together to talk about exploits and hacks they have discovered. Many companies work feverishly in the hours after a presentation to fix the vulnerabilities discuss during DEFCON. Custom electronic “badges” with blinking lights are sold all over the place.

DEFCON Villages
Villages are a staple of DEFCON. Most conferences are filled to the brim with presentations. When preparing for my first DEFCON, everyone told me to not pay attention to the presentations, but to focus instead of the content in the Villages. Because of those recommendations, I looked forward to the villages the most in attending my first DEFCON experience.
Before the Villages opened, the first day had a very good presentation about the Evolution of Cellular Networks. It was recorded and hopefully will be uploaded to DEFCON Youtube Channel at a later date. I highly recommend it. HackerPinUp had the largest following of questions afterward out of any session that I saw.

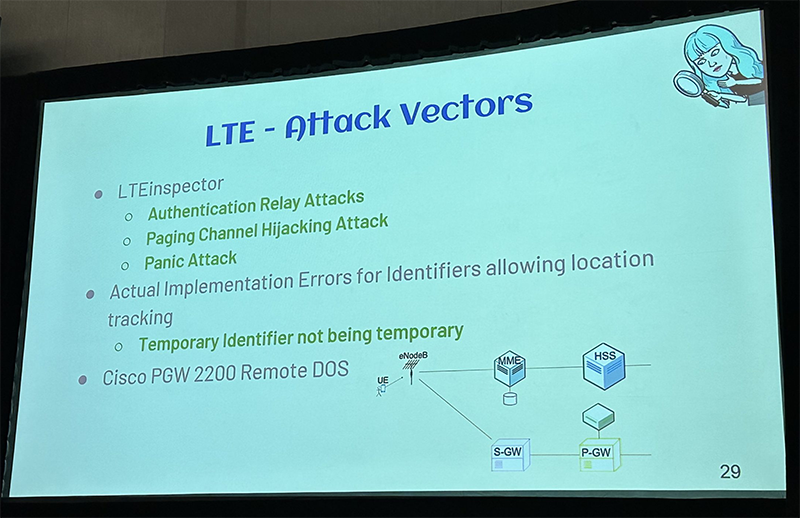
She talked about IMSI-Catchers, Core Designs and Architechtures, Downgrade Attacks, Rogue NodeBs, 5G SUPI and SUCI, and Mitigations.
DEFCON 31 had two Villages that most interested me, Radio Frequency Village and the Telcom Village; the later being a new addition to this year’s conference.
In the RF Village, hackers and researchers played with the latest technologies for hacking Wifi and other wireless technologies. SDR and Antennas were everywhere. Presentations about vulnerabilities with Wifi, including chatter about the long broken WEP and WPA as well as vulnerabilities in WPA2 and WPA3.
The brand new Telcom Village focused on the different Gs of the cellular world. Each day presented different vulnerabilities associated with each G. The first day was 2G/3G vulnerabilities with SS7 attacks. The second day was about 4G LTE and attacks on the Diameter protocol. The last day focused on 5G vulnerabilities and protections. Non of the presentations focused specifically on Private Cellular and there wasn’t a Private Cellular network running at the conference. I hope that changes for future cons.
SAINTCON
Every year for the last nine years, I have attended a local smaller version of DEFCON called SAINTCON put on by some good buddies at my day job. Many of the GOONs from DEFCON created an education version in St. George, Utah that has slowly grown to the current size of about 2,500 attendees and moved to Provo, Utah in October. SAINTCON has grown from the humble beginnings of education to include hackers and security researchers from all industries and fields.
The Villages idea was brought to SAINTCON several years ago, and continues to grow if a Village fits.
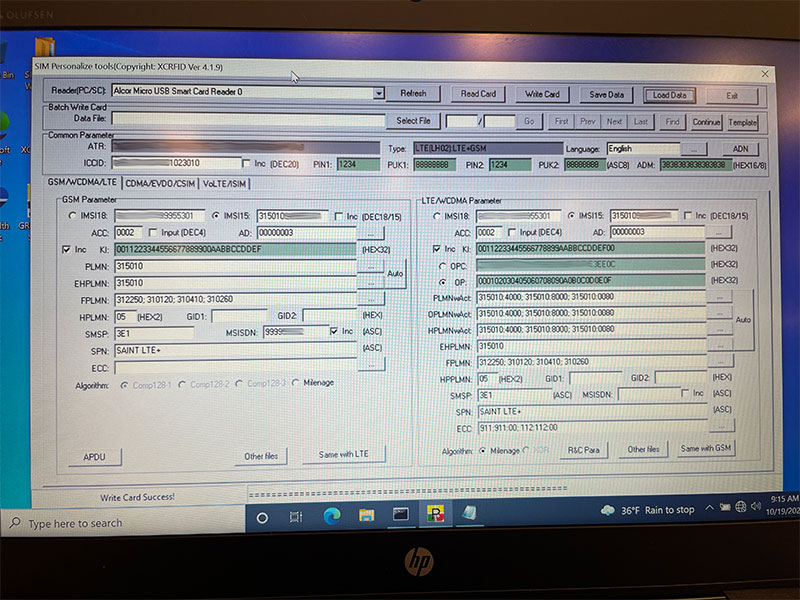
Two years ago, and returning this year, we had our own version of the Telecom Village that we called the Private LTE Village. We had on site our Private LTE network including CBRS radios that reached into some of the neighboring hotels.
We trained conference attendees on how to program a physical SIM card that they could put in their devices if it supported Band 48. We invited and had many people attempt to hack the Private LTE network including many CTFs challenges. One group of interested hackers put a network tap inline to one of the radios to gather information about the core network. It was a very interesting experiment.
DEFCON and SAINTCON Badges
One thing that sets DEFCON and SAINTCON apart from many other tech conferences are the nerdy badges everyone carriers around their necks. This year’s main conference badge was a let down to many because it lacked anything electronic and the badge was easily counterfeited. That didn’t stop thousands of custom electronic badges being sold around the conference though. I picked up the Car Hacking Badge with red and blue blinking LED lights.

My friend got the incredible Heart Badge to honor his daughter from the BioHacking Village. The Heart Badge had a sensor like the Apple Watch that would sensor the wear’s heartbeat and sync the LED lights according to the wear’s heartbeat.
Badge life brings out some crazy custom PCB designs.
WLAN Pi Pro + 5G Modem Backpack
Inspiration, from years of attending SAINTCON, gave me the idea of using the WLAN Pi Pro as my own badge. As I’ll explain in shortly, the WLAN Pi Pro is used for Scanning Wifi networks with the two Intel AX210 chips. I added a “Backpack” to the WLAN Pi Pro with a 5G Modem card with a 3D printed case.
My badge garnered a ton of interest from those around me as soon as I put it on. There certainly is a growing interest in understanding how cellular networks work and testing them. Private Cellular Networks are the solution to avoid the legal issues around gathering data about public cellular networks.
Wifi Scanning
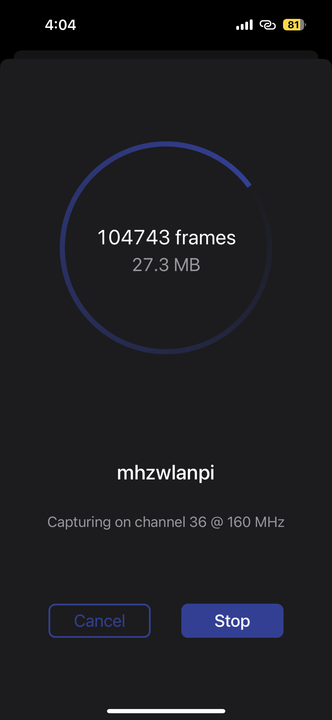
While walking around the Villages area in the LINQ, I decided to see what could be captured on both the Wifi Bands and CBRS Band. I didn’t want to carry around a Laptop. So, I connected up my iPhone to the WLAN Pi Pro using Bluetooth.
Using Adrian Granados’ Airtool Pi App, I started capturing Wifi Frames. The tool is limited to only capturing on a specific channel. So, I selected a channel that is likely to be used by the highest number of devices, Channel 36 at 160MHz wide. I started the Capture and got 104,743 Frames in my PCAP file after walking around for a few minutes.
The conference network because it is a large group of hackers is questionable on the security front. Because of that, they provide an EAP-PEAP credential and certificate that individually encrypts the traffic for a user’s devices instead of using the same Pre-Shared Key for the encryption keys on the Wifi.
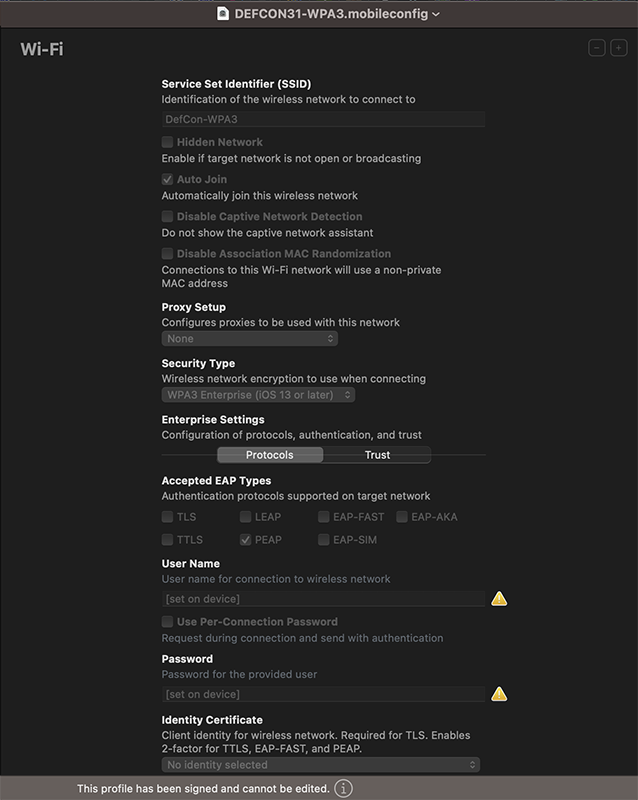
They had 4 SSIDs broadcast for the conference specifically. DefCon-WPA3, DefCon, DefCon-Open, and a hidden SSID.
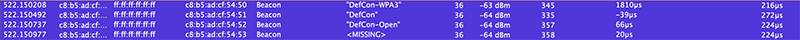
Because we are hackers, the recommended conference network was running the more secure version of WPA3-Enterprise instead of WPA2-Enterprise. They weren’t using the most secure version of WPA3-Enterprise which is WPA3-Enterprise 192-Bit, but WPA3-Enterprise provides pretty good security. While many said to avoid the network all together, only using the WPA3-Enterprise network would provide good enough security for most.
On the wired side, they said they built a Zero Trust Network. Trust that as much as you will. There was an interesting annoyance more than a hack that involved Bluetooth and an Apple TV vulnerability that supposedly only was done to bug people rather than steal data.
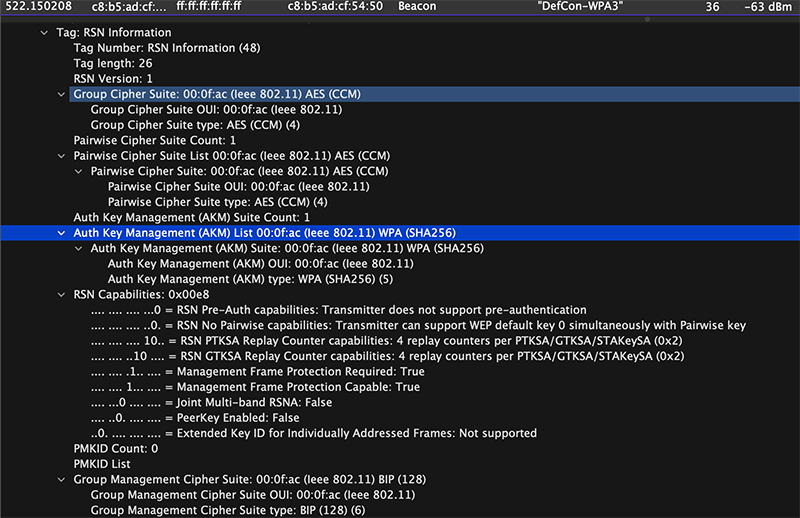
It is not recommended to use the other two Wifi networks at the conference. DefCon was a regular WPA2-PSK network. It wasn’t even running WPA3-SAE Transition Mode.
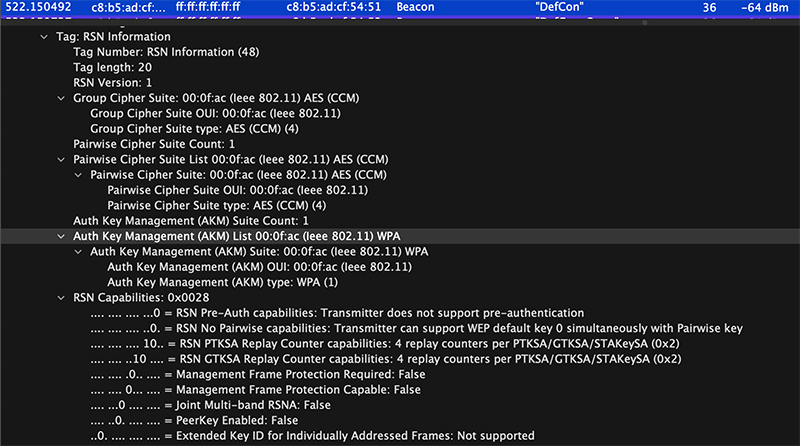
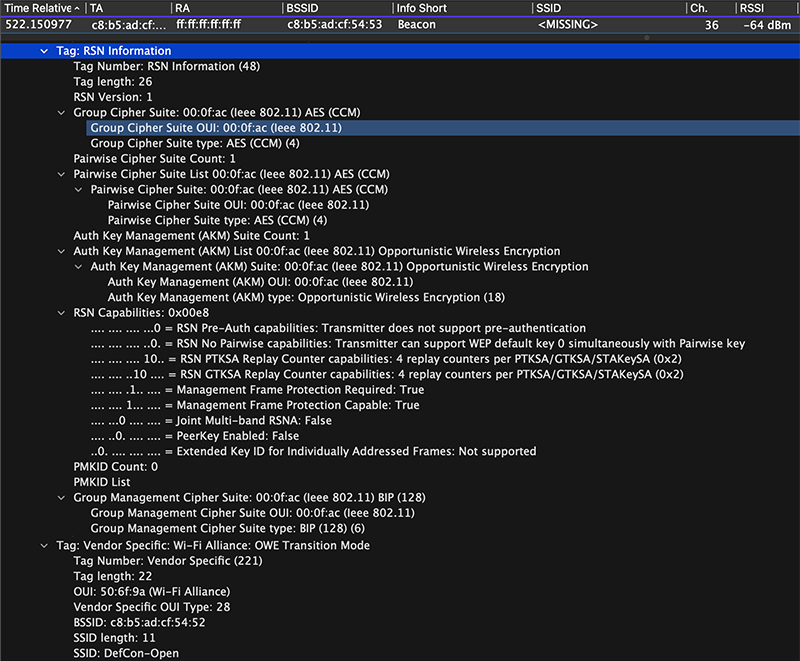
The DefCon-Open SSID is as they said on their website the “Wild West” when it comes to secure networks. DefCon-Open was just that, an Open SSID. It was running Enhanced Open also called Opportunistic Wireless Encryption (OWE) Transition Mode. With Transition mode, if a device supports OWE it will use it, if it doesn’t it will use a regular Open Authentication which has no encryption. There is no “RSN Information” Element included with OWE. There is the “Vendor Specific: Wi-Fi Alliance: OWE Transition Mode” Tag at the bottom of the capture that tells you it was using OWE.
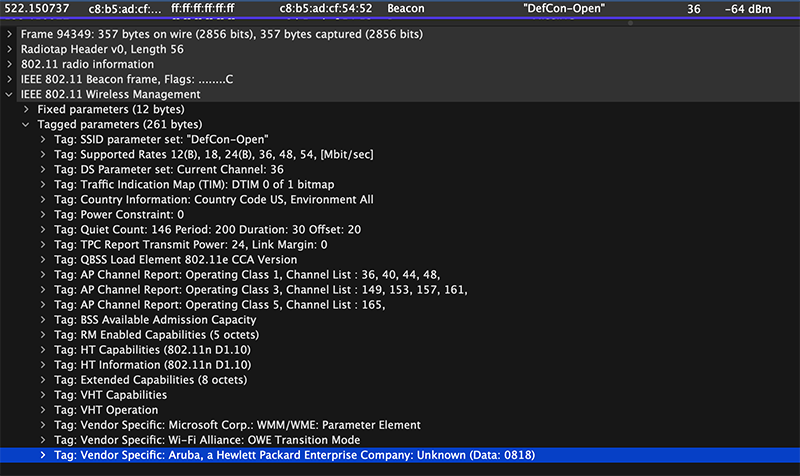
When using Open Enhanced/OWE Transition Mode, it requires a separate Hidden SSID. That is where the “<Missing>” SSID comes from. At the bottom of the capture is the information about OWE Transition Mode that ties this hidden SSID to the DefCon-Open SSID.
Every year, DefCon has a display called the “Wall of Sheep” that displays credentials and leaked information that were sent unencrypted and captured during the Con. Most of that data was captured by unsuspecting people using the Open SSID (not the OWE one) or being decrypted on the WPA2-PSK network. In actuality, most of the data that ends up on the Wall of Sheep is most likely trolls that did it on purpose.
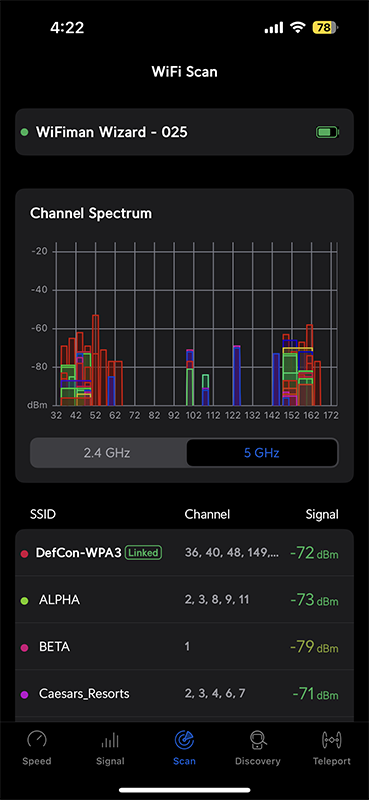
Another interesting part was the different SSIDs that I found throughout the conference. There were SSIDs called GAMMA, ALPHA, BETA, DELTA, VIP, and OMEGA being broadcast by the venue from the same APs. Some are WPA2-PSK and others are WPA2-Enterprise. The venue didn’t seem to be running any WPA3 networks yet.
Beyond what the venue and conference were using, I picked up a bunch of random SSIDs all over the place. I captured “I_LOVE_SUGAR_Secure” and “I_LOVE_SUGAR_Toast” A LOT! It’s always fun to see some of the names of SSIDs.
I also had another tool in my belt at DEFCON. While I had a burner Macbook Pro with Wifi Explorer Pro with me, I didn’t dare use it. Instead, I had a Ubiquiti Spectrum Analyzer that attached to the back of the iPhone Magsafe and connects over bluetooth. That gave me the two images below of the 2.4GHz and 5GHz bands. Sadly, it doesn’t support 6GHz, and I wasn’t able to find if any 6GHz SSIDs were being used.
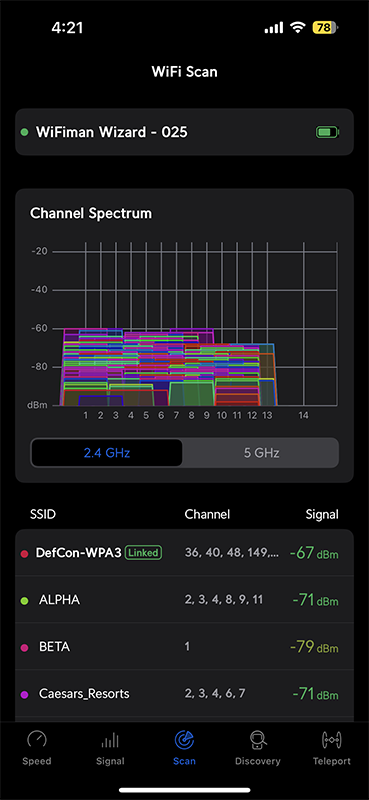
At least in that area of the conference, many of the DFS channels were not being used. I’ve heard stories that some of the DFS channels in Las Vegas are used by Radar at the nearby Airport. Those DFS channels are unusable by Wifi and that may account for some of the lack of usage of those channels.
4G LTE Scanning
While I was running Airtool Pi on my iPhone capturing the Wifi data, I was also connected to the WLAN Pi Pro with an SSH session using Terminus. I have a 5G Modem “Backpack” attached to the 1/4-20 head mount screw on the back of the WLAN Pi Pro. The 5G board I bought doesn’t come with a case. So, I designed and 3D printed my own case and included a hole for a 1/4-20 screw that I got off Amazon. The 5G Backpack just screws on the back and connects using the USB-C port. I didn’t have the USB cable connected when I took these pictures.
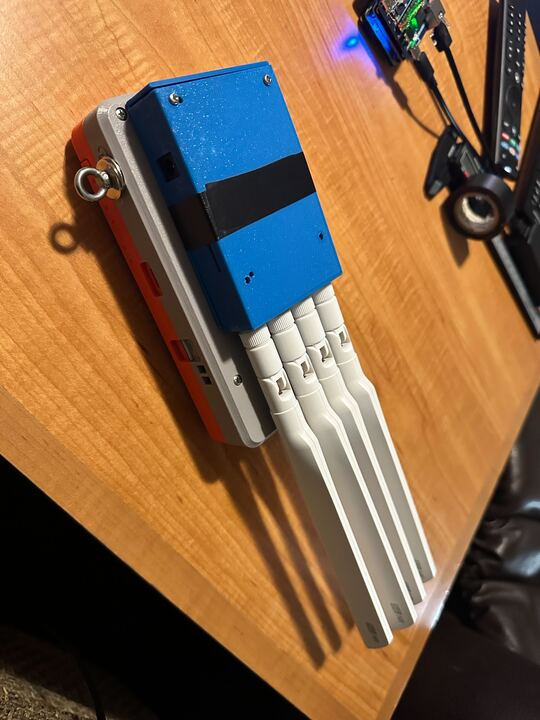
The board I found has a port for a barrel power plug but it can be powered off the USB-C port. I’ll explain in a future blog post more about the specific modem and how this is setup and connected.

Walking around DEFCON, I started the SCAT application from Github. I’ve done some modifications to the output to create a CSV file. The developers recently updated the repository and have modified it significantly. It looks like they are working to add 5G measurements to SCAT. A future post I’ll explain what I did with modifying the results to output to a CSV file. The output of my modified version looks like this:
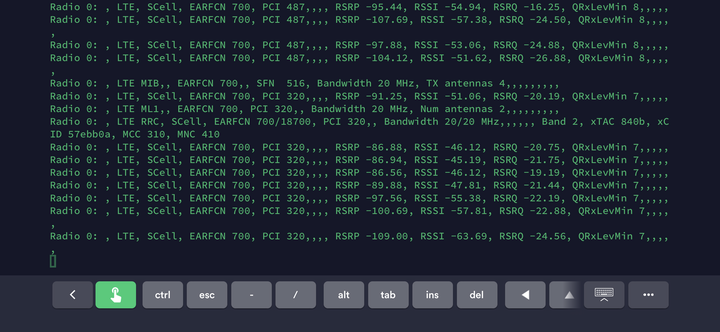
As I was wandering around the Villages, I was hoping that the Telecom Village had a Private Cellular CBRS network. I quickly discovered that they did not. So in order to get some results, I added a few bands beyond Band 41 and Band 48 to my scanning as I explaining in this previous blog post.
Before modifying the Bands, SCAT was returning zero results. That simple change fixed the scanning and it started to return some Band 2 information with EARFCN 700. It also soon returned the MCC and MNC for which carrier was broadcasting on Band 2. In the above screen shot is MCC 310 and MNC 410. This is the MCC/MNC of AT&T.
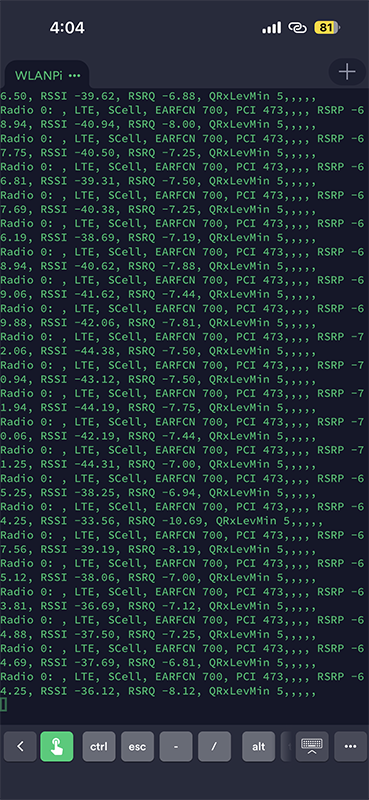
I was capturing live on the screen the EARFCN, PCI, RSRP, RSSI, RSRQ, and QRxLevMin that I can now output to a CSV file. That information can now be plotted into a map and used later. In the above screenshot you’ll notice that there was a change in the PCI or Physical Cell ID. That is when my device selected a new radio on the same Band 2. I was able to capture how strong the signal was received by my device to a log file.
The other cool thing about SCAT is that it outputs that information to the screen or file, but it ALSO can capture a PCAP. This is the PCAP that I captured while wandering around the Villages. It only captured information from Band 2 AT&T but there is some useful information included.
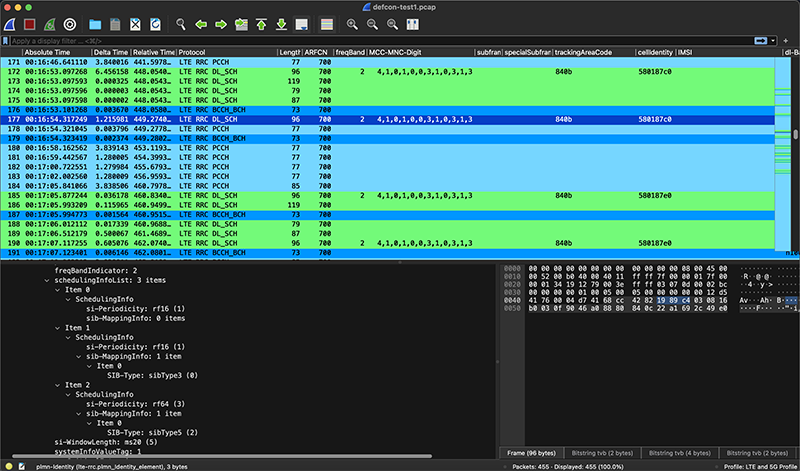
My device does not have a SIM installed during these surveys. The AT&T signal data was all just captured unencrypted from what was heard on Band 2 by the device. If I had a SIM installed it would have attempted to join the AT&T network and display the more information about the LTE MIB, SIB1, SIB3, and SIB5.
I’m hoping that DEFCON next year has a Private Cellular network like we built a couple years ago at SAINTCON. I also hope that the Telecom Village expands and grows. I have some ideas for a CTF for next year that would be fun to build.
Findings
Overall, I had a blast at DEFCON 31. I met some amazing people and learned a ton. While my device has more of an IT focus, the things being discussed at Security conferences can relate to the IT world. There doesn’t have to be silos between the NOC and SOC.

Was the captured survey data extremely useful? Perhaps not. BUT it was sure fun to play with and see what is happening around the con. Especially when those networks are not the most trusted.
Hacking hardware, like the custom badges, is exactly what those of us building these tools are doing. We are taking something and using it in a way for which it wasn’t designed. The Raspberry Pi was definitely not designed to be a Cellular Survey tool nor was it designed to be an Earthquake Seismograph. It was designed to let people play and discover. All those badges at DEFCON and SAINTCON come from that same mantra.


